NOVANEWS
ZIO=NAZI officer suspected of covering up Gaza killing
Commander allegedly attempted to block probe by not giving a report on the death of a Palestinian woman to Military Advocate-General Mandelblit.
An IDF commander is suspected of blocking an investigation into the death of a Palestinian in Gaza, according to reports released on Thursday.
The officer is suspected of not submitting the results of a probe about a woman killed when she approached a Givati Brigade station during Operation Cast Lead.
Military Police is investigating the case, which involves officers in the Rotem battalion of the Givati Brigade, who were supposed to give a report to Military Advocate-General Maj.-Gen. Avichai Mandelblit.
The oversight was revealed during the trial of S., the soldier accused of killing the Palestinian woman in the report. S.’s case was opened in April 2010, when a reserve officer said that he found the report, which had not been transferred to Mandelblit, on an IDF laptop computer.
The soldier’s lawyers have demanded that the trial be stopped until Military Police finish investigating the commanders in the case.
Iran: We successfully test-fired local S-300 system
Revolution Guards commander says system developed by upgrading Russian-made S-200; not clear when missile test took place
Iran announced Thursday it had successfully test-fired an air defense system similar in its capabilities to the Russian S-300 system, the state-run PRESS TV network reported.
“We have developed the system by upgrading systems like S-200 and we have tested it successfully using all our potential and experience in the Islamic Revolution Guards Corps, the Army and the Defense Ministry,” Brigadier General Mohammad Hassan Mansourian was quoted as saying.
Mansourian did not say when the missile test took place, but Iran is currently holding a large-scale air defense drill simulating attacks on its nuclear facilities.
Moscow recently canceled a deal involving the sale of the S-300 system to Iran on grounds that it violates UN sanctions aimed at penalizing the Islamic Republic over its nuclear program.
As a result, relations between Moscow and Tehran have deteriorated.
In the 1980s Iran purchased the S-200 surface-to-air missile system from the former Soviet Union.
Site exposes IDF ‘war criminals’
Website reveals details of hundreds of Israeli soldiers it claims took part in Gaza war. ‘I stand by everything I did in Operation Cast Lead, and I have nothing to be ashamed of,’ says First Sergeant (res.) Ziv Danieli, one of toops included on the list.
A website that went online Tuesday has published a list of 200 IDF soldiers which it classifies as directly involved in operations carried out in Gaza during Operation Cast Lead. Each entry features the soldiers and officers’ pictures and personal details, including identification numbers and addresses.
“In underlining them we are purposefully directing attention to individuals rather than the static structures through which they operate,” the website states while calling on visitors to spread the info “widely”. The reliability of the information is as yet unclear.
“Underlining the following people is an act of retribution and affront. They are the direct perpetrators, agents for the state of Israel that in Dec. – Jan. 2008- 2009 attacked scores of people in the besieged Gaza” noted the website. The website has no special design or graphics, just a table of names of soldiers listed in alphabetic order which the site claims, served in the army in the winter of 2008-2009.
Soldiers listed include officers from the very top of the IDF hierarchy – Chief of Staff Gabi Ashkenazi and down to a sergeant in the infantry training program.
“The people listed here held positions of command at the time of the attack therefore not only did they perform on behalf of a murderous state mechanism but actively encouraged other people to do the same. They bear a distinctive personal responsibility. They range from low-level field commanders to the highest echelons of the Israeli army. All took an active and direct role in the offensive,” claimed the website.
A website counter at the top of the page states that over 3000 people have viewed the website so far. They claim that the information “was received anonymously; presumably from a member of the Israeli Military”.
It seems that the information was collected via the internet, doubtlessly through extensive use of social networks. A quick search reveals that many of the pictures on the site, especially those of the younger low level soldiers, were taken from facebook profiles.
“This information was pirated. We encourage people to seek out other such similar information, it is readily available in the public sphere and inside public officials’ locked cabinets,” they said. The person or group behind the website remains a mystery as does the level of exposure that the website receives.
The reliability of the information displayed is also in question, since other than in the case of the senior officers listed, it is impossible to tell whether those listed even served in the IDF during Operation Cast Lead.
“In underlining them we are purposefully directing attention to individuals rather than the static structures through which they operate. We are aligning people with actions. It is to these persons and others, like them, to which we must object and bring our plaints to bear upon”, they further stated.
The project organizers declare that “this is a form of resistance that can be effectively sustained for a long while”. Visitors to the website are told that “this project for one, has only just begun, do your bit so that this virtual list may come to bear upon the physical”. The manifest signs off by calling all web surfers to get involved and: “Disseminate widely”.
Ynet has discovered that many of the details appearing on the website are correct. The photos were taken from various news publications and social networks like facebok. The officers and soldiers aren’t quite sure how their details got into the website’s hands, but clarified that they were proud of their actions and happy to be included in the list.
Danieli doesn’t know where the website got his personal information from but he stressed that he had no problem with the website. “Enjoy it! Whoever wants to can talk to me, I’ll share my phone number as well if they want it. I stand by everything I did in Operation Cast Lead; I have nothing to be ashamed of.”
‘The enemy within’
Danieli thinks that Israeli sources are behind the site. “The same people that the State protects are those that go out against it; sadly the enemy is within, as if we didn’t have enough problems from outside.” He isn’t worried about harassment: It doesn’t scare me, it doesn’t bother me, I have taken trips abroad and will continue to do so, and more than that, I would be happy to meet whoever is behind the site.”
Noam Kashivski who served as a deputy tank company commander was also surprised to see his picture and personal information on the website. “I don’t know who these people are but I’m at peace with my actions,” he told Ynet.
“I guess they found some of the information illegally, my picture was taken from my facebook account,” Kashivsky added and claimed that this was nothing more than a political attack: “The site lists no sources and no details are added, they just rushed to a conclusion that suited them.”
Kashivsky said that he was “happy and proud to be on the list next to honorable men and women,” adding that he wouldn’t change his ways because of the site. “I’m not afraid, and I won’t avoid going abroad. The orders we received were all honorable and necessary, I have no regrets.”
The site which is operated through British servers has already raised furious responses. An Israeli organization called My Israel has already picked up the gauntlet – offering 10,000 shekels ($2,712) to “anyone who will present information that will lead to catching those responsible for the website calling IDF soldiers ‘war criminals’ and responsible for publishing their personal information.”
The IDF spokesman stated that the army “is distressed over the publication of the names and information of 200 officers and soldiers under the heading of ‘war criminals’ slandering them and their reputations without any concrete evidence whatsoever.”
In small US Muslim enclave, a plea to pray in peace
Omar Karmi, AP
SIOUX FALLS, SOUTH DAKOTA–Just across from the front door inside the Islamic Centre of Sioux Falls there is a sign that reads: “We should all be free to pray.”
In this sparsely furnished single-storey building, with its otherwise bare white walls, the exhortation stands out.
Contrary to what might at first be thought, the appeal is not directed at the overwhelmingly white and Christian population of this blue-collar neighbourhood in Sioux Falls, South Dakota’s largest city, with an estimated population in 2009 of 150,000. Rather, the injunction reflects the highly diverse nature of the city’s small, but rapidly growing, Muslim community.
From 15 in 1990, there are now almost 3,000 Muslims improbably tucked away in the eastern-most city of this Midwestern state, most famous for the 1890 Massacre at Wounded Knee, where 150 Sioux prisoners were killed by United States cavalry, finally breaking Native American resistance to the colonial expansion of the US.
It is a population that has grown largely as a result of an influx of refugees, many fleeing fighting in Somalia, Ethiopia and, increasingly, Iraq. Combined with other more traditional economic immigrants, the Sioux Falls Muslim community is an almost perfect microcosm of the Muslim world.
However, this diversity has brought its own problems. Until last year, the classroom-sized masjid at the centre was the only Muslim prayer room in the state to cater to the growing numbers of Muslims. To date, it remains the larger of only two, both in Sioux Falls.
“We are a very mixed community,” said Mohammad al Ostaz, a Palestinian, who left Kuwait in 1987 to study physical therapy in Sioux Falls. “But we’re not a Pakistani or an Arab mosque. There are differences between us, and we’ve all had to learn to get along,” he added by way of explanation of the sign at the door.
“There is a lot of ignorance about Muslims here,” he said after Maghreb prayers on the first day of Eid. “There are a lot of stereotypes.”
Unable to return to Kuwait after the first Gulf War, Mr Ostaz, 43, stayed in South Dakota. Though he never finished his studies, he eventually started his own translation service that now handles more than 100 languages. In his 23 years here, he said, he has always experienced negative stereotypes about Arabs and Muslims.
The stereotypes have changed – for the worse, he said. “They used to be about camels and oil and having four wives. Now, they are about terrorism and violence. The stereotypes were always negative, they’ve just become more so.”
The negative views have been reflected in nationwide polls. In August, the Pew Forum on Religion and Public Life found that the number of Americans with a favourable view of Islam had dropped from 41 per cent to 30 since 2005. The percentage of those with an unfavourable view had climbed from 36 to 38 per cent in the same period.
Perhaps, more tellingly, the poll counted just 62 per cent of Americans who believe Muslims should have the same rights as other groups to build houses of worship in their local communities, with 25 per cent opposed and 13 undecided.
And, at times, what Ibrahim Hooper of the Council on American Muslim Relations calls an “alarming rise in anti-Muslim sentiment” finds violent expression, with instances of hate crimes becoming more prevalent. In Sioux Falls, such incidents have been rare. After the September 11 attacks, someone smeared faeces on the door handle of the Islamic Centre, Mr Ostaz said. People have called in threatening messages and a brick was thrown through the window.
Yousef al Kafiti, 47, who has lived in Sioux Falls since 1992, said he too had noticed the change. “My wife covers her hair, and we hear a lot of comments in shops like, ‘Go home to where you’re from, you don’t belong here’,” said Mr Kafiti, who is of Libyan origin. His wife is an American convert to Islam. “Even if there are no comments, I can often feel the dirty looks.”
There have been efforts at outreach from the Muslim and Christian communities. Mr Ostaz said he had participated in a number of talks to residents in Sioux Falls, mostly arranged by local churches. “They’ve been much more organised about this than us.”
He also remembered with “great admiration” a day when a local family, on an apparent whim, had come on their own to the Islamic Centre to learn about Islam.
Moreover, he said, his business had never suffered. “I never felt that anything but my competence was at issue in work. In fact, in 2006, I had my best ever year.”
Mr Kafiti, who has worked for 16 years in the same plastics factory, said that while September 11 had caused a lot of harm to the Muslim community, it had also caused people to want to learn more about Islam.
“Eventually they see I’m just like them. I came to this free country to build my life and work hard.”
[email protected]
Son of Stuxnet? Variants of the cyberweapon likely, senators told
The Stuxnet cyberworm could soon be modified to attack vital industrial facilities in the US and abroad, cybersecurity experts warned Wednesday at a Senate hearing.
Iran’s facility at Natanz, about 200 miles south of Tehran, is reported to have been infected with the Stuxnet worm.
Stuxnet, the first known weaponized software designed to destroy a specific industrial process, could soon be modified to target an array of industrial systems in the US and abroad, cyber experts told US senators Wednesday.
The Stuxnet malware, discovered this summer, was apparently designed to strike one target – Iran’s nuclear-fuel centrifuge facilities, researchers now say. But Stuxnet’s “digital warhead,” they caution, could be copied and altered by others to wreak havoc on a much grander scale.
Variants of Stuxnet could target a host of critical infrastructure, from the power grid and water supplies to transportation systems, four cybersecurity experts told the Senate Committee on Homeland Security and Governmental Affairs.
“The concern for the future of Stuxnet is that the underlying code could be adapted to target a broader range of control systems in any number of critical infrastructure sectors,” said Sean McGurk, acting director of the National Cyber-security and Communications Integration Center at the US Department of Homeland Security.
Stuxnet infiltrated and targeted an industrial control system software that is widely used in US infrastructure and industry, meaning the nation is vulnerable to future Stuxnet-like attacks, he said. “While we do not know which process was the intended target [of Stuxnet], it is important to note that the combination of Windows operating software and Siemens hardware can be used in control systems across critical infrastructure sectors – from automobile assembly lines to mixing baby formula to processing chemicals,” said Mr. McGurk.
Citing his research at the national lab, Mr. Assante noted that his team there had explored a similar avenue earlier – alluding apparently to a 2007 test that used Internet-delivered commands to destroy a diesel generator – prompting black smoke and bolts flying off the machine. “I have participated in research that demonstrated this capability in a controlled environment to understand how it could be done,” he said. “I believe that the analysis to date has indicated that Stuxnet may be such a weapon.”
Concern about vulnerability of the power grid has led to warnings and new standards. Yet the grid remains vulnerable to a Stuxnet-style threat, Assante asserted. New government standards have become a “glass ceiling” for companies to perfunctorily meet, he said, but not to exceed.
The Department of Homeland Security (DHS) and a team at the national lab have reverse-engineered and decoded Stuxnet, McGurk said. But DHS is worried that attackers “could use publicly available information about the code” to develop variants targeted at broader installations of programmable equipment in control systems, he said.
That statement may well be a slap at Symantec, which published detailed reports on precisely how Stuxnet works. Bulletins from DHS, on the other hand, omitted key details, said several cybersecurity researchers interviewed by the Monitor.
Still, lack of information-sharing is preventing readiness to combat advanced cyberthreats like Stuxnet, said other witnesses at the hearing.
“A significant cause for concern is that much of the information about cybersecurity-related threats remains classified in the homeland security, defense, and intelligence communities, with restricted opportunity to share information with security researchers, technology providers, and affected private-sector asset owners,” Assante said. Restricted use of newly gained knowledge about advanced cyberthreats, he added, places “our nation’s critical infrastructure is placed at significant risk.”
The witnesses gave varying assessments about how prepared the private sector is to deal with a threat of Stuxnet’s sophistication.
Mark Gandy, global cybersecurity chief for Dow Corning Corp. and chairman of the American Chemistry Council’s cybersecurity steering committee, said industry is working hard and is up to the task.
“The chemical sector understands this evolving threat,” he said. “The ACC and its members have been working for years across the sector to prepare and share information about these issues…. We continue to comprehensively improve control system security.”
Assante, sounding much less enthusiastic about industry preparedness, cited technology trends that make it easier for attackers to strike control systems.
“I believe we’re extremely susceptible,” he said. “In fact, I believe our susceptibility grows every day. If you just look at the very trends in the technology that we deploy, we’re doing things that would allow an attacker more freedom of action within these environments…. Stuxnet is an important harbinger of things that may come if we do not use this opportunity to learn about this threat and apply it.”
As of last week, 44,000 computers worldwide were still infected with the Stuxnet worm – including 1,600 in the US, said Dean Turner, head of global intelligence for Symantec Corp., the computer security firm that detailed Stuxnet’s inner workings. Fifty of those US infections had worked their way from Windows operating systems into industrial control systems. It’s not publicly known who created Stuxnet.
“Our level of preparedness … in the private sector is better than it ever has been, but still has a long way to go,” said Mr. Turner. “It’s a cliché, but we don’t know what we don’t know.”
Perhaps the sharpest alarm was sounded by Michael Assante, president of the National Board of Information Security Examiners. He’s seen the threat up close, having held key posts in industrial control system security research at the Idaho National Laboratory and then as chief security officer of the North American Electric Reliability Corp., which is charged with power grid reliability.
“Stuxnet is, at the very least, an important wake-up call for digitally enhanced and reliant countries – at its worst, a blueprint for future attackers,” he said. It is a “good example of a cyberthreat thought to be hypothetically possible, but not considered probable by many.” Its sophistication “should disturb security professionals, engineers, businessmen, and government leaders alike.”
related–Stuxnet Computer Worm–Israel’s Attempt To Silence Iran on 9/11 or Veiled Threat to the Entire World?
Cyber Attacks Present ‘Huge’ Threat, Gates Says
By Elaine Wilson
American Forces Press Service
WASHINGTON, Nov. 17, 2010 – Leaders are taking steps to bring defense industrial and domestic partners under an umbrella of protection from cyber attacks, Defense Secretary Robert M. Gates said.
|






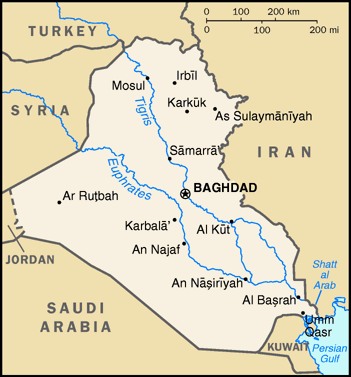 The idea of the province, which would be carved out of the portion of the Nineveh Province bordering Iraqi Kurdistan,
The idea of the province, which would be carved out of the portion of the Nineveh Province bordering Iraqi Kurdistan, 

